Helping you to protect your business in the cloud
Design better websites and spend less time without restricting creative freedom. Combine layouts, customize everything.
Cloud securitythrough partnership


The Cloud Security to help your business thrive
Combine seamlessly fitting layouts, customize everything you want, switch components on the go using our page builder.
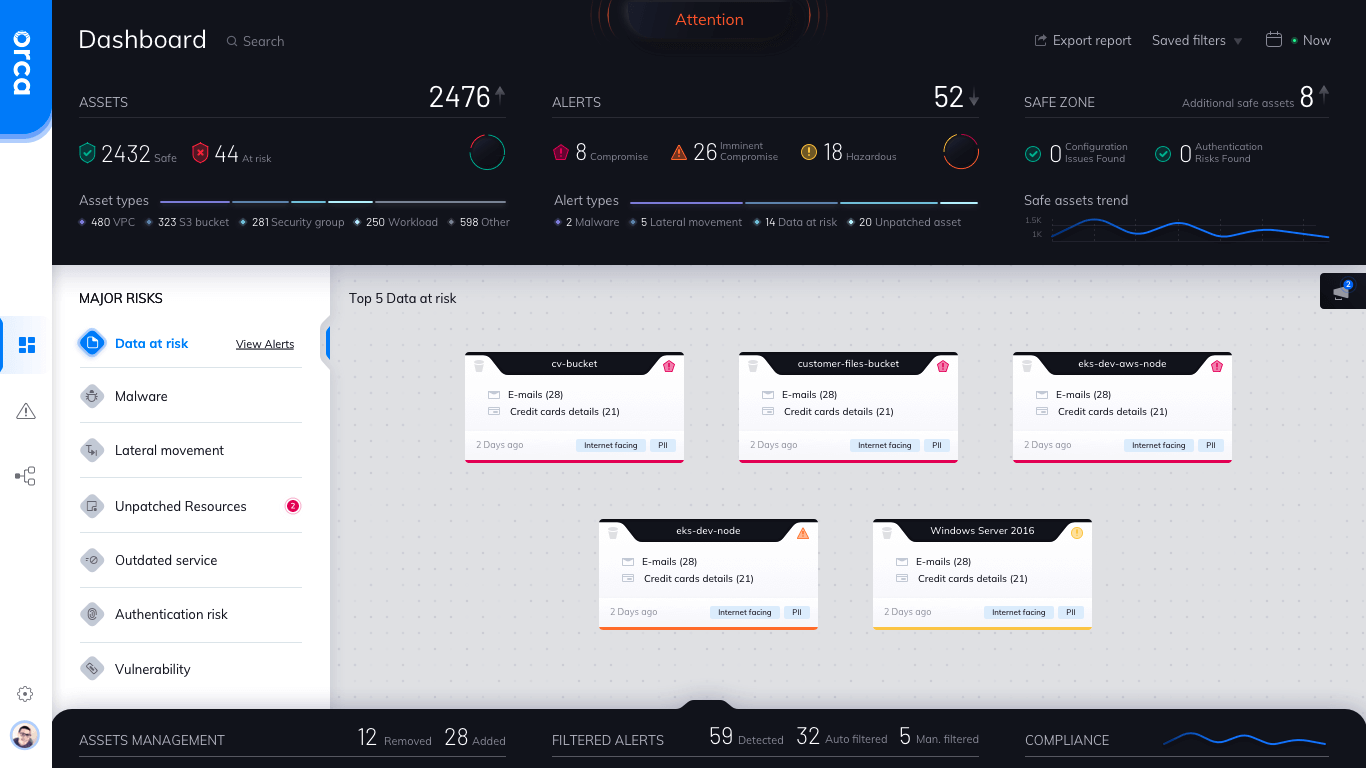
Unify cloud security in a single platform
Orca brings together core cloud security capabilities, including vulnerability management, multi-cloud compliance and posture management, cloud workload protection, container security, and more in a single, purpose-built solution.
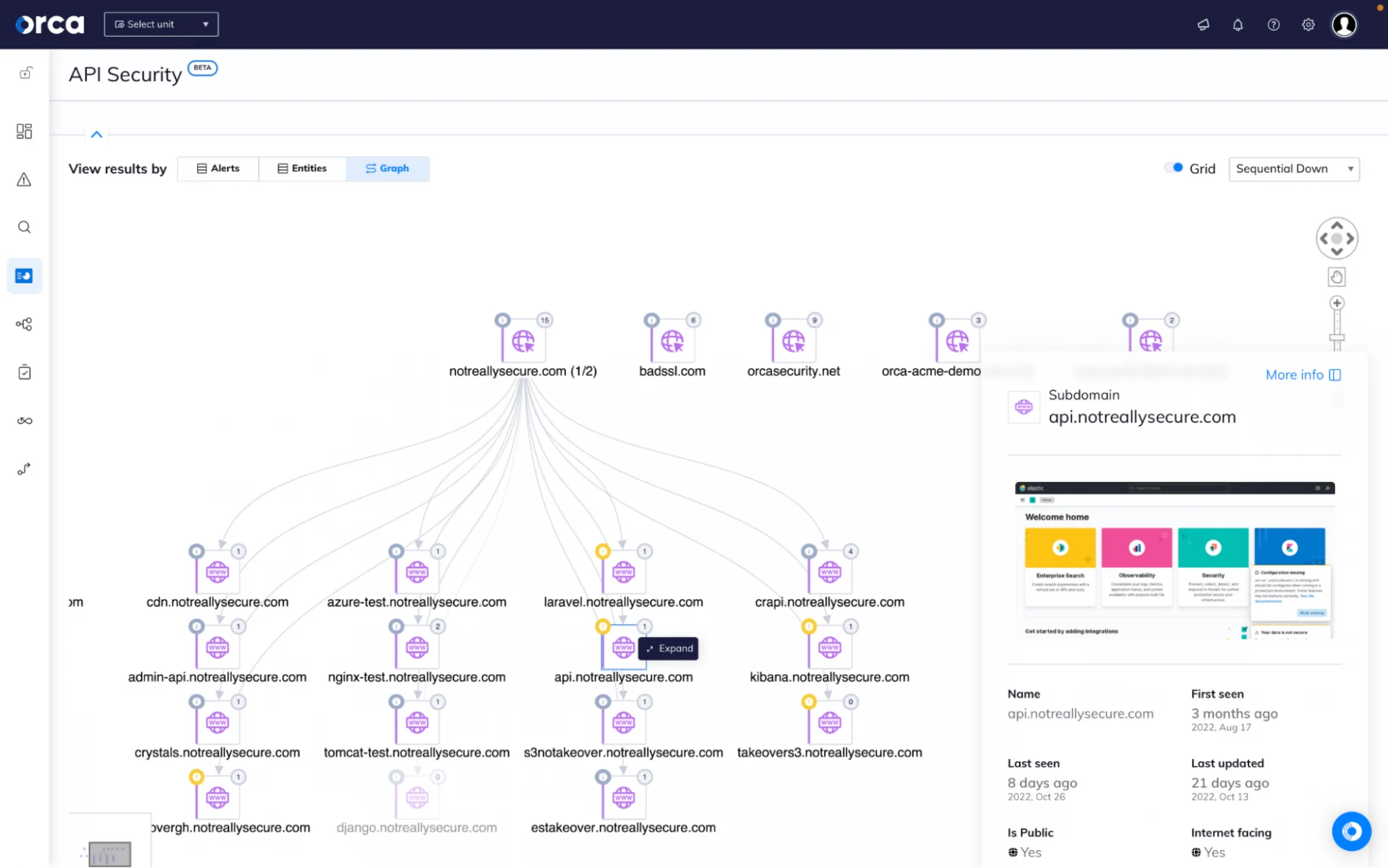
We prioritize alerts so you don't have to
Unlike other tools that operate in silos, Orca sees the big picture and prioritizes risk based on context, eliminating wasted time sifting through meaningless alerts and enabling you to focus on the 1% of truly critical issues.
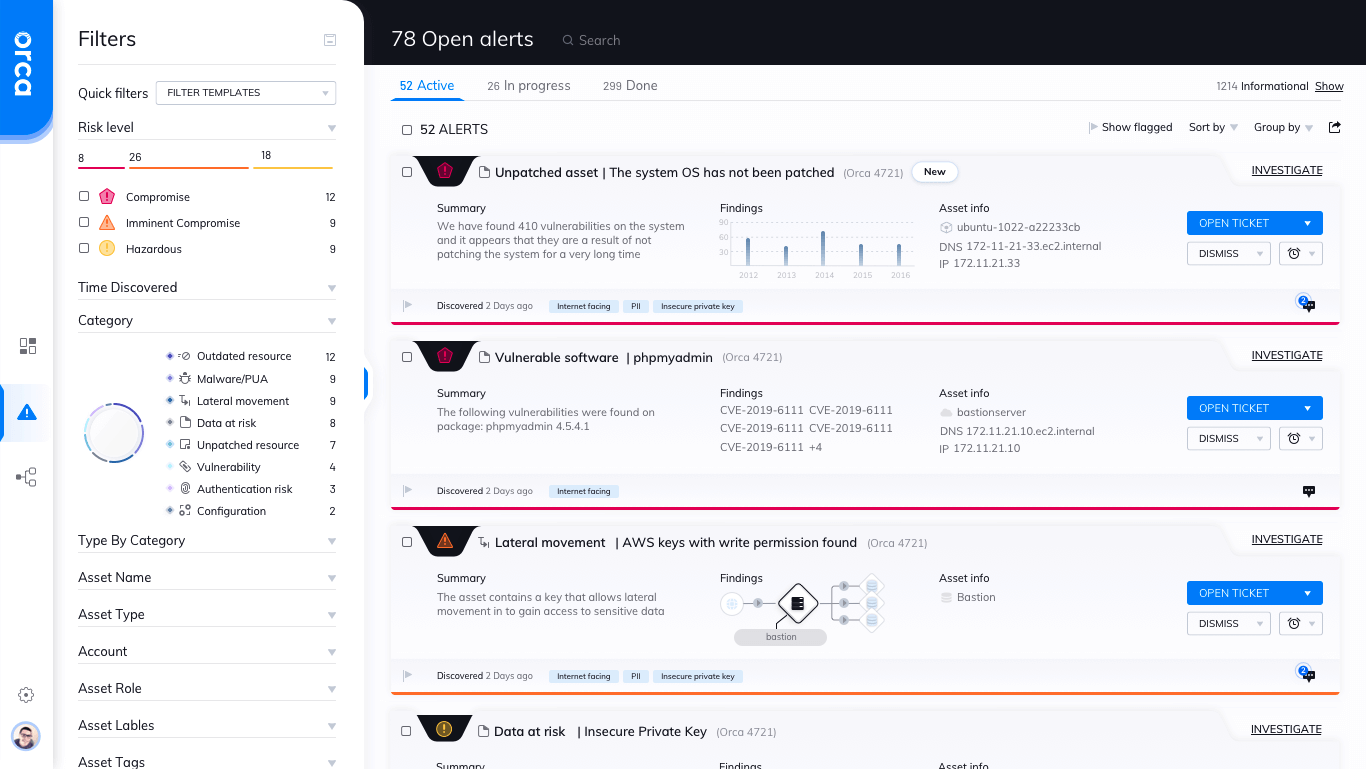
Get your business ahead of the threats
With Orca Security and Raftech, stay ahead of the ever-evolving cyber threats that could impact your business.
Explore the Orca Cloud Security Platform
Combine seamlessly fitting layouts, customize everything you want, switch components on the go!