Keeping our digital spaces secure is crucial, especially in a massive and always-changing platform like Amazon Web Services (AWS). As cyber threats get more complicated, it's vital to have strong security in place to protect our information, programs, and systems. AWS Identity and Access Management (IAM) is like the guardian of security in AWS. It gives us detailed control over who can access what. But IAM doesn't do this job alone; it teams up with other AWS services to make sure our entire setup stays safe and sound.
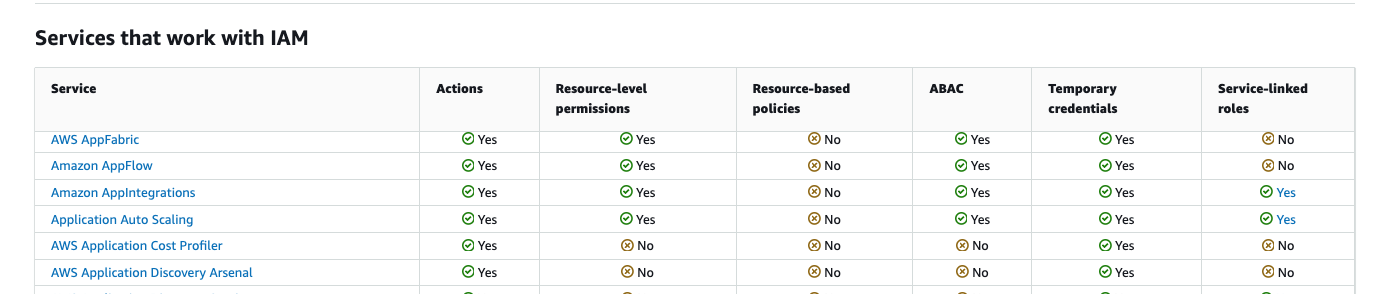
There are different levels of integration between the specific AWS services and IAM. Each of these integration capabilities will dictate what results and with what effort you will be able to achieve.
Service Authorization:
- Each AWS service supports different actions that users can perform. You can find detailed documentation on IAM authorization and access for each service.
- Actions are specific tasks that users can do within a service. Some services allow fine-grained control over individual actions, while others have broader permissions like "All actions."
Resource-Level Permissions:
- IAM allows you to specify permissions for individual resources using Amazon Resource Names (ARNs). This means you can control access to specific resources within a service.
- However, not all services support this feature for every resource type. Some actions, like listing resources, don't support specifying individual ARNs.
Resource-Based Policies:
- Some services allow you to attach policies directly to resources. These policies determine which IAM identities can access the resource.
- Resource-based policies include a Principal element to specify IAM identities.
Authorization Based on Tags (ABAC):
- You can control access based on tags attached to resources. This is done by defining conditions in IAM policies using specific condition keys.
- Some services fully support ABAC, while others only support it for certain resource types.
Temporary Credentials:
- IAM allows you to generate short-term credentials for accessing AWS services. These credentials are obtained through IAM Identity Center, role switching, or AWS Security Token Service (STS).
- Long-term IAM user credentials (like username/password or access keys) are necessary for accessing services that don't support temporary credentials.
Service-Linked Roles:
- Service-linked roles are special roles that grant permissions to AWS services to access resources on your behalf.
- Not all services support service-linked roles. You can find documentation for services that do support these roles.
The why it matters
While you could wonder why this matters, the simple answer is that you must be aware of limitations when you plan for security architecture, i.e., ABAC or locking down security on a specific set of resources.
This is where the following AWS document will provide you with the matrix of services and their supported IAM configurations